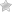How to make Plesk WordPress instantly more secure
For our hosting customers, we do a lot to make WordPress websites safer:
- We automatically block bots and visitors from IP addresses that display suspicious activity.
- Hits with malicious query strings are blocked by the server. #
- On request, we can create a further security barrier between the website and the Internet, a so-called Web Application Firewall.
- In consultation with you, we regularly perform backups and updates.
But there are also some things you can do yourself: Logged in to your technical customer area (Plesk Admin) for your website/s you as a customer can perform our Plesk WordPress Security Check – which is by no means as well known as it deserves.
Common security gaps of a fundamental nature that exist in many WordPress installations can be eliminated immediately by you in this way.
Below we would like to explain briefly what the Security Check can do for you.
You will find the Security Check under “WordPress” in the main menu:
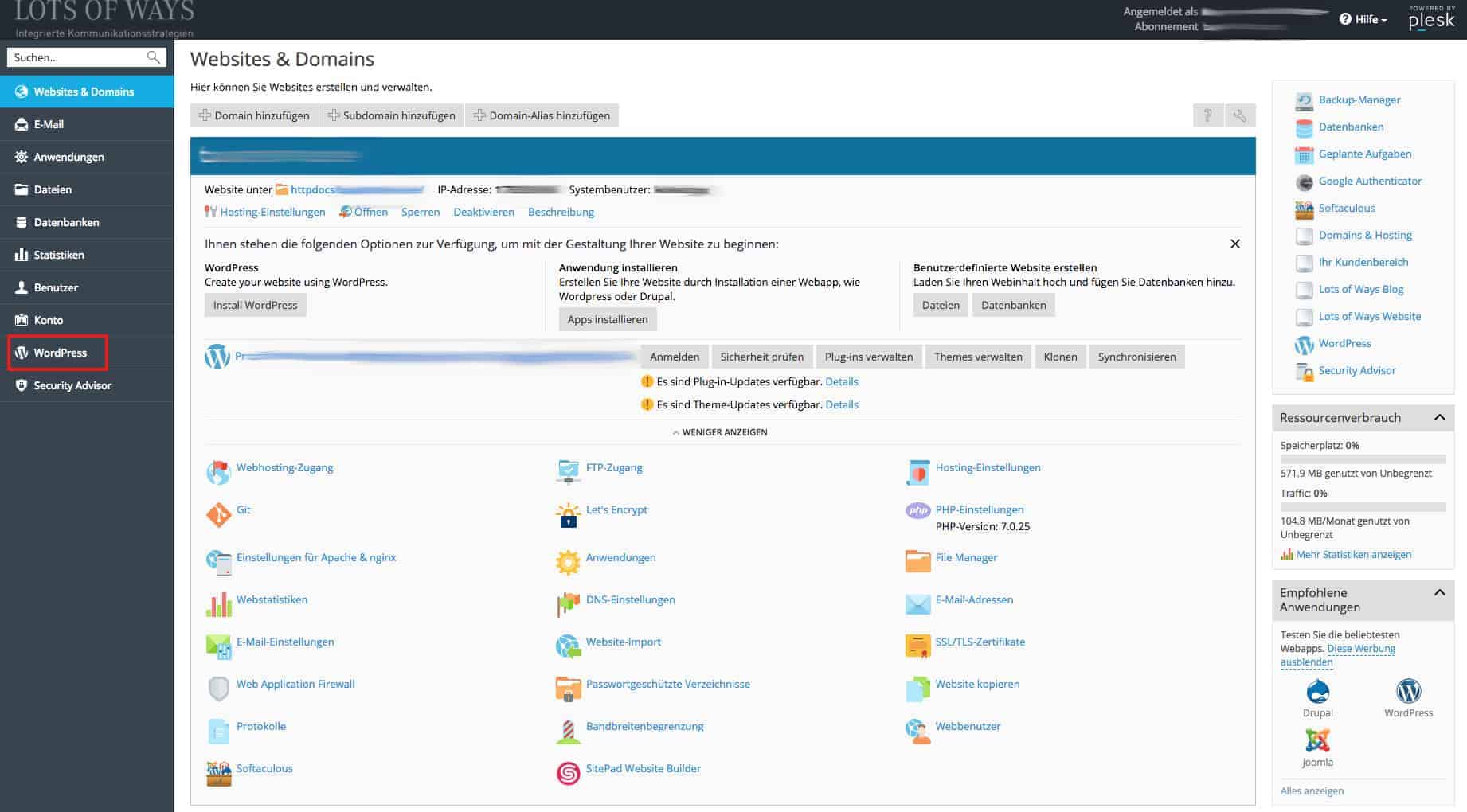
These recommendations are provided by the WordPress Security Check:
User name of the administrator
If WordPress is installed, there is a user with administrator rights and the login name’ admin’. A bad idea. Hackers know that too. Attackers only have to guess the password to the user “Admin” to access the system as administrator. And since this “guessing” does not take place manually, but with the help of powerful scripts, it leads to success sooner or later without special protective measures.
Plesk’s security check checks whether there is a user with administrator rights and the login name’ admin’. If this is the case, they will be warned and should change this.
Normally not so easy – you would have to make changes in the database and think of all sorts of things. However, Plesk can do this security optimization for you automatically:
- New user is created with a random login name and password as well as the same profile and properties as the administrator.
- The contributions and links of the administrator are then assigned to the new user.
- The previous administrator account with the treacherous name is removed.
.
Database Prefix
If the default prefix of your WordPress database is’ wp_’, this is the default “ex works”. That is a safety disadvantage. Plesk checks whether the prefix for database table names is not’ wp_’. If this is the case, Plesk will do the following for you on request:
- Maintenance mode is switched on
- All plugins are deactivated
- The prefix in the configuration file is changed
- The prefix in the database is changed, the plugins are reactivated
- The permalink structure is updated
- Maintenance mode switched off again
.
Security of the configuration file
The file’ wp-config.php’ contains access data for the database etc. Whoever has access to this file controls a WordPress website immediately without restriction.
After installing WordPress, this file can be executed. She has to. However, if for some reason the processing of PHP files by the web server is disabled, hackers can access the content of wp-config.php. Then it’s no longer funny.
Plesk checks whether unauthorized access to the wp-config is possible.
If desired, security problems can be automatically fixed with the ‘wp-config.php’.
Directory search permissions
When directory search is turned on, hackers can retrieve information from your site. The Bad Guys flick through your directories, see which plugins you are using and what kind of usable data is lying around on your web server. You don’t want that. Therefore, this Security Check function deactivates the directory search.
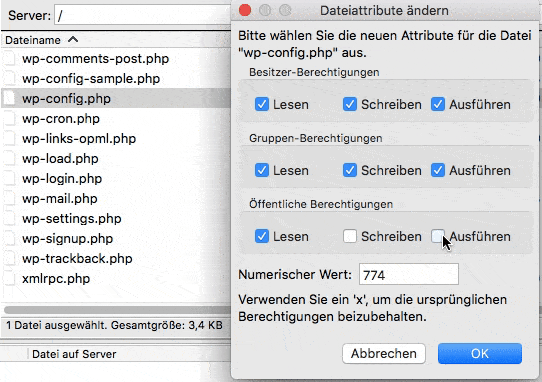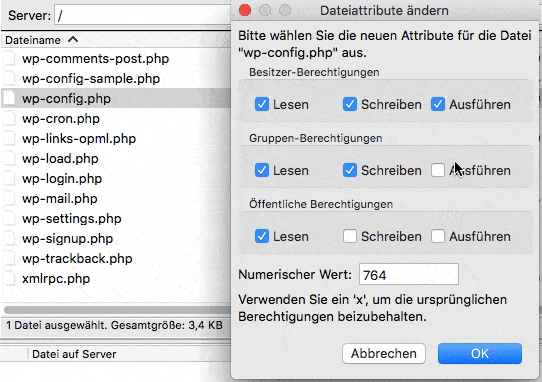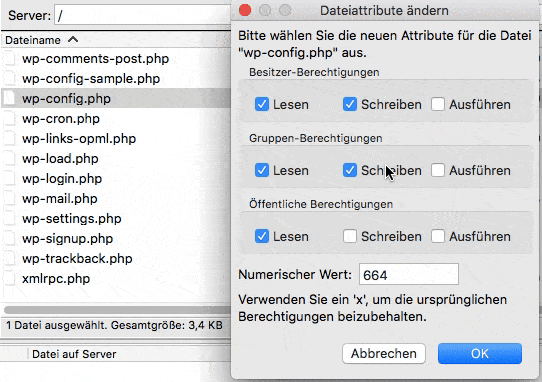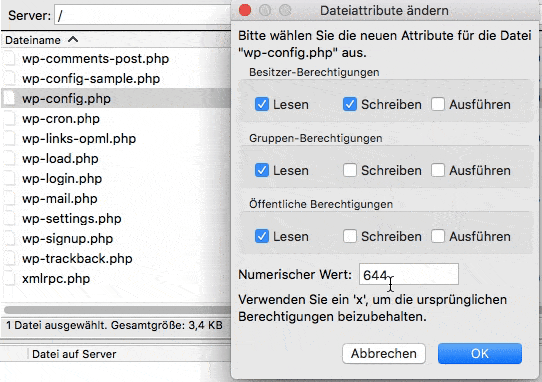
Permissions for Files and Directories
After installing WordPress, files and directories can have permissions to permissive permissions. Plesk checks whether the permissions for the file’ wp-config’ are set to 600, for other files to 644 and for directories to 755. If this is not the case, the security script sets the appropriate permissions automatically.
Security Keys
WordPress uses security keys (AUTH_KEY, SECURE_AUTH_KEY, LOGGED_IN_KEY and NONCE_KEY) to ensure better encryption of information stored in a user’s cookies. A good security key is
- long (60 characters or more)
- randomly compiled.
The security check checks whether the security keys are set up and contain at least letters and numbers. If the security check fails and you decide to increase the security of the WordPress installation, secure security keys are generated and added to your WordPress installation.

Security of the wp-content folder
The’ wp-content’ directory can contain insecure PHP files. Normally the PHP files can be executed in this directory. If desired, Plesk prevents files from running in’ wp-content’. The server configuration file prohibits the execution of PHP files in the directory’ wp-content’. Note that custom statements in the. htaccess or web. config files may override this.
Security of the wp-includes folder
The same applies to’ wp-includes’. Files in this path are executable after the WordPress installation. It doesn’t have to stay that way. Plesk can prohibit execution of PHP files in the’ wp-includes’ directory. Note, however, that user-defined statements in the files’. htaccess’ or’ web. config’ may overwrite this.
Disable XML RPC Pingbacks
XML RPC pingbacks can be used to launch DDoS attacks on other WordPress sites. This security measure disables XML-RPC pingbacks for the entire WordPress website. It also disables pingbacks for previously created posts with activated pingbacks.